Use of Digital Signature
The main operations within the project; *Entrance
- Why Java?
- Why OpenAPI
- How to compile the project.
- Smart Card Transactions
- Certificate Information Reading
- Obtaining Smart Card Information
- Obtaining Certificate Information
- Certificate Information Reading
- Signature Processing
- First Type Signing (Direct file signing)
- Second Type of Signing (Signing the Hash information of the file)
- Cades Signing
- Integrated signature
- Split signature
- Serial signature
- Parallel signature
- Cades Signature Verification
- Pades Signing
- Integrated Signature
- Pades Signature Verification
- Xades Signing
- Integrated signature
- Split signature
- Serial signature
- Parallel signature
- Enveloped Signature
- Xades Signature Verification
- Signature archiving
- Signature upgrade
- Advanced Signature Verification
- Test Operations
- Signature Test
- Integrated signature
- Split signature
- Serial signature
- Parallel signature
- Signature Verification Test
- Verification of Signed Document
- Signature Upgrade Tests
- Signature Test
- Possible Errors
- Future Enhancements
- Supported/Unsupported File Types and Signature Types
- How You Can Contribute
Introduction
The Digital Signature project is a project that meets the transactions you want to perform with e-signature in a basic sense. One of the reasons why we took out the project was to eliminate the lack of documents, applications and information related to the use of e-signatures in our country. In this context, you can learn the source codes of the project we have developed, the necessary explanations, how the project works, which signature types it supports, the areas that can be developed in the project and what our future developments are in detail from this document.
The Digital Signature project is a project that provides an electronic signature feature. Using the Api tips of the E-signature system developed by Tübitak, it performs signing, signature verification and signature upgrade operations for PDF(Pades), XML(Xades) and Cades document types valid for all formats. The Digital Signature project is a ready-to-use library for you, and you can easily sign when you build the project. In addition, the Digital Signature project has a wide alternative structure. After integrating the project, you can perform signing operations on your servers and provide a high level of data security.
The Digital Signature project is currently able to process BES-EST-ESXLONG and ESA signature types.
As a working structure, it is to perform the signature process by pulling the necessary information from the USB Dungle (e-signature) installed on your Computer with the command you send from your Internet browser. The following image illustrates this in detail.
Figure 1- 1. Type Signature
Figure 2- 2. Type Signature
Why Java
As mentioned above, the Digital Signature project supports Cades, Pades and Xades formats. Among these formats, Pades type (used to sign pdf documents.) uses iText pdf processing library in its infrastructure. Project dependencies require the iText library to be provided separately. However, the iText library requires a license on .NET platforms. For this reason, Pades signing is not available in the "E-signature" .NET library developed by Tübitak. In short, the iText library does not require licenses on Java platforms. Pades signature is also available in the "E-signature" Java library developed by Tübitak. For this reason, the Java project has been developed.
Why OpenAPI
Thanks to the Open structure, the Digital Signature project has universal access. A software developer anywhere in the world can access the API and perform any integration they want. Thus, the integration of the Digital Signature project has become much easier. In addition, software developers can use the features of the Digital Signature project with less coding, and the small amount of code written minimizes the complexity of the program. This ensures that possible errors caused by code are minimized.
How to compile the project.
In order to run this project that you downloaded from Github, you need to have an application, jdk, installed on your computer that can compile Java. The project was developed as Maven and SpringBoot was used in it. In this way, compilation operations can be done in a simple way without the need for statement operations.
>The file structure of the Digital Signature project is as follows.
>When we open the project in Visual Studio Code, we see a structure as follows.
> In the VS code project opened, dscore-1.0.0 and restapi-1.0.0 projects under Maven should be clean install and compile respectively.
After these operations you can Run our project.
Smart Card Transactions
Reading Certificate Information
To read the certificate information, it is first necessary to retrieve the list of smart cards that are inserted into the computer. A GET request is thrown to the "getTerminals" method of the "SmartCardController" class to retrieve the list of Smart Cards.
Importing Smart Card Information
''sh http://localhost:3638/api/smartcard/getTerminals
**Response returned from Get request; **
The returned answers come in Base64 format.
''sh
[
{
"terminal": "QUNTIEFDUjM5VSBJQ0MgUmVhZGVyIDA=",
"library": "YWtpc3AxMQ==",
"slotId": "MQ=="
}
]
The returned values are described in the following table.
| Feature | Description | Value (base64) | Value (string) |
|---|---|---|---|
| terminal | The name of the inserted smart card. | "QUNTIEFDUjM5VSBJQ0MgUmVhZGVyIDA=" | ACS ACR39U ICC Reader 0 |
| Library | Card Type | YWtpc3AxMQ== | AKISP11 |
| slotId Drive | PortId information of the card that is installed | MQ== | 1 |
> Library and SlotId are required to Read a certificate and sign from a smart card.
Obtaining Certificate Information
A POST request is made to the "getCertificates" method of the "SmartCardController" class to pull the certificate information. The information to be sent in the POST request is shown in the following example.
Request Address
''sh http://localhost:3638/api/smartcard/getCertificates
**Request Content**
```>``` The library and slotId information in the request are the values returned from the getTerminals method.
''sh
{
"library": "YWtpc3AxMQ==",
"slotId": "MQ==",
"onlyQualifiedCertificates": true
}
Answer Information
> Returned values are masked for privacy.
''sh [ { "certificateHex": "3e43500069001000730028663687474703a...", "subjectSerialNumber": "NDA2...", "serialNumber": "MzM...", "commonName": "Q049RVJPTCBF...", "isExpired": "Zm...", "issuer": "Q049VMOcUktUUlVTJ...", "issuerCommonName": "VMOcUktU...", "notAfter": "MjAyMy...", "notBefore": "MjAyM...", "subjectCommonName": "RVJP...", "subject": "Q049RVJ..." } ]
```>``` Of this information, **certificateHex** will use **serialNumber** in the signing process.
| Feature | Description |
|---------------------|-----------------------------------------|
| certificateHex | It is the information of the Certifika in hex format. |
| subjectSerialNumber | Card Type |
| serialNumber | TC Identity Number |
| commonName | Location, First NameSurname and SeriNumber |
| isExpired | Validity Status |
| issuer | Manufacturer Information |
| issuerCommonName | Manufacturer Information |
| notAfter | Certificate Expiration Date |
| notBefore | Certificate Acquisition Date |
| subjectCommonName | Certified Holder Name Surname Information |
| subject | PortId information of the card that is installed |
## Signature Processing
There are 2 different ways to sign in the KamuSM - Digital Signature project. One of them is to sign by sending the file information directly, and the other is to sign by creating the hash information of the file we will sign. (This method consists of 3 different processes in total.)
```>``` Two different signing features are also available for all types (Cades-Xades-Pades).
### **First Type Signing**
In order to sign the first type, it will be sufficient to make a request to the **sign** method in CadesController, XadesController, PadesController.
**Request Address**
```>``` A request should be made to whichever type of signature is desired.
''sh
First Type Signature
http://localhost:3638/api/cades/sign
http://localhost:3638/api/xades/sign
http://localhost:3638/api/pades/sign
Request Content
> The library and slotId information in the request are the values returned from the getTerminals method.
The certificateHex and certificateSerialNumber information in the request are the values returned from the getCertificates method.
''sh { "certificateHex": "3e43500069001000730028663687474703a", "file": "MIKyYQYJKoZIhvcNAQc...", "embeddedSignature": true, "isCounter": true, "signatureType": 2, "timeStampHost": "timeStampHost", "timeStampUser": "timeStampUser", "timeStampPassword": "timeStampPass", "library": "YWtpc3AxMQ", "slotId": "MQ==", "certificateSerialNumber": "MzM...", "pin": "123456" }
| Feature | Description |
|-------------------------|-----------------------------------------|
| certificateHex | It is the information of the Certifika in hex format. |
| file | File to sign in Base64 format |
| embeddedSignature | Integrated or Disjoint Signature information |
| isCounter | Serial and Parallel signature information |
| signatureType | signature type (Bes-Est-Esxlong-Esa) |
| timeStampHost | Timestamp host address |
| timeStampUser | Timestamp username |
| timeStampPassword | Timestamp password |
| Library | Smart card library information |
| slotId | Smart card's slot information |
| certificateSerialNumber | Certificate Serial Number |
| Pin | Smart card password information |
**Answer Information**
```>``` The rotating format for the First and Second types of signing is the same.
''sh
A signed document in Base64 format is returned.
Second Type Signing
The second type of signing is the signing made by creating the hash information of the file and sending it to the signer. When signing a file, the file and the signer may not always work in the same place. For this reason, instead of sending the entire file to the signer, sending hash information of the file will be more efficient in terms of data size. A second type of signing method has been developed to meet this need.
- InitializeSigning
- Sign
- FinalizeSigning
InitializeSigning
> A request should be made to whichever type of signature is desired.
Request Address
''sh Second Type of Signing http://localhost:3638/api/cades/initializeSigning http://localhost:3638/api/xades/initializeSigning http://localhost:3638/api/pades/initializeSigning
**Request Content**
''sh
{
"key": "test-123",
"certificateHex": "{{certificate}}",
"file": "dGVzdCBkb2vDvG1hbiBkZW5lbWUgaW16YQ==",
"existSignature": "dGVzdCBkb2vDvG1hbiBkZW5lbWUgaW16YQ==",
"embeddedSignature": true,
"signatureType": 0,
"isCounter": true,
"timeStampHost": "timeStampHost",
"timeStampUser": "timeStampUser",
"timeStampPassword": "timeStampPass"
}
| Feature | Description |
|---|---|
| key | ........... |
| certificateHex | It is the information of the Certifika in hex format. |
| file | File to sign in Base64 format |
| existSignature | Split signature information of a previously signed file in base64 format |
| embeddedSignature | Integrated or Disjoint Signature information |
| isCounter | Serial and Parallel signature information |
| signatureType | signature type (Bes-Est-Esxlong-Esa) |
| timeStampHost | Timestamp host address |
| timeStampUser | Timestamp username |
| timeStampPassword | Timestamp Password |
Answer Information
''sh { "digestToBeSigned": "/w9slx2VTf2oq36fFcJDW4ny/vae0I2v0gG5f1V8ze/++mMw4AD", "transactionUUID": "63D1770A9143729C62962FC5599D0609D709343D5E299D8E71" }
| Feature | Description |
|------------------|---------------------------------------------|
| digestToBeSigned | Hash info |
| transactionUUID | Initialize(initiated) process UUID |
**Sign**
```>``` We sign our Initialize request.
**Request Address**
''sh
http://localhost:3638/api/smartcard/sign
Request Content
''sh { "data": "/w9slx2VTf2oq36fFcJDW4ny/vae0I2v0gG5f1V8ze/++mMw4AD", "library": "YWtpc3AxMQ", "slotId": "MQ==", "certificateSerialNumber": "MzM...", "pin": "123456" }
| Feature | Description |
|---------|-------------------------------------------------------------|
| data | digestToBeSigned information returned from the InitializeSigning method |
| Library | Card Type |
| slotId | PortId information of the card that is installed |
| Pin | Smart card password |
**Answer Information**
''sh
{
"signedData" = "Q5eaPK/4RPUhDJlzioDsNo6SxFojpBRe9ivC+Ss0rVI"
}
| Feature | Description |
|---|---|
| signedData | It is the hash information of the document signed in base64 format. |
FinalizeSigning
Request Address
''sh http://localhost:3638/api/sign/finalizeSigning
**Request Content**
''sh
{
"key":"63D1770A9143729C62962FC5599D0609D709343D5E299D8E71",
"signatureData":"Q5eaPK/4RPUhDJlzioDsNo6SxFojpBRe9ivC+Ss0rVI"
}
| Feature | Description |
|---|---|
| key | Initialize(initiated) process UUID |
| signatureData | It is the hash information of the document signed in base64 format. |
Answer Information
''sh Signed Document in Base64 format "MIIK8wYJKoZIhvcNAQcCoIIK5DCCCuACAQExDTALBglghkgBZQMEAgMwKAYJKoZIhvcNAQcBoBsEGXRlc3QgZG9r"
## **Using Mobile Signatures**
### Signature Processes
There is only one way to sign a signature in the KamuSM - Mobile Signature project. This way is to sign by creating the hash information of the file we are going to sign. (This method consists of 2 different operations.)
```>``` supports Cades and Padesi. It does not currently support Xades.
### **Mobile Signature Methods**
* InitializeMobileSigning
* FinalizeMobileSigning
**InitializeMobileSigning**
```>``` A request should be made to whichever type of signature is desired.
**Request Address**
''sh
http://localhost:3638/api/cades/initializeMobileSigning
http://localhost:3638/api/pades/initializeMobileSigning
Request Content
''sh { "key": "test-123", "certificateHex": "", "file": "dGVzdCBkb2vDvG1hbiBkZW5lbWUgaW16YQ==", "embeddedSignature": true, "signatureType": 0, "timeStampHost": "timeStampHost", "timeStampUser": "timeStampUser", "timeStampPassword": "timeStampPass", "phoneNumber": "05012345678", "messageToShow": "Mobile signature is for testing purposes only", "gatewayAddress": "http://MImzaBimser", "mobileOperatorType": 0 }
| Feature | Description |
|--------------------|-------------------------------------------------------------------------|
| key | ........... |
| certificateHex | It is the information of the Certifika in hex format. |
| file | File to sign in Base64 format |
| existSignature | Split signature information of a previously signed file in base64 format |
| embeddedSignature | Integrated or Disjoint Signature information |
| signatureType | signature type (Bes-Est-Esxlong-Esa) |
| timeStampHost | Timestamp host address |
| timeStampUser | Timestamp username |
| timeStampPassword | Timestamp Password |
| phoneNumber | Phone number with mobile signature authorization |
| messageToShow | Message to appear when giving confirmation on the phone screen |
| gatewayAddress | Address information allowed by telecom companies |
| mobileOperatorType | 0 for Turkcell, 1 for TurkTelekom 2 for Vodafone |
**Answer Information**
''sh
{
"transactionUUID": "63D1770A9143729C62962FC5599D0609D709343D5E299D8E71",
"fingerPrint": "9BAF22AF41BD7B9D1B892A2664044BA2C436EBD8DEC404A3521BFC680138914CEC1927B974ABA87E3D6859F74AFC212123B9D3598DD3592A471C6C573565C33A"
}
| Feature | Description |
|---|---|
| transactionUUID | Initialize(initiated) process UUID |
| fingerPrint | Code block sent to phone for verification |
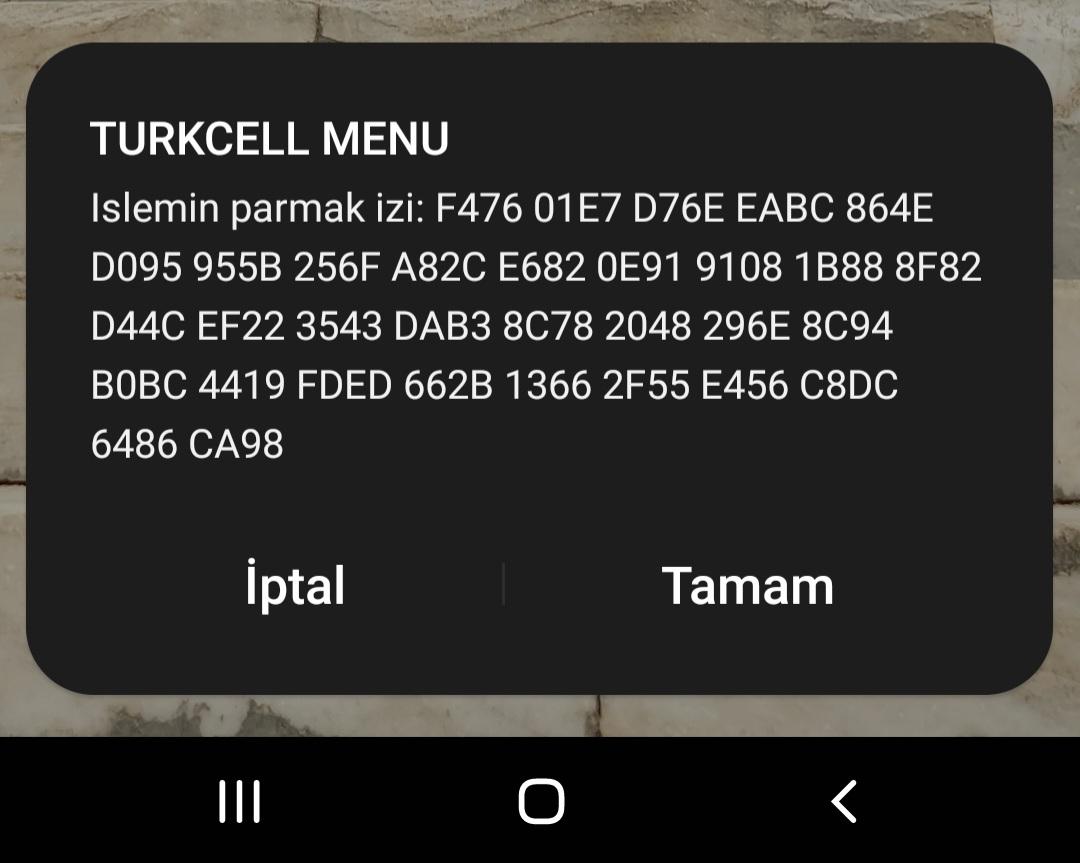
FinalizeMobileSigning
Request Address
''sh http://localhost:3638/api/sign/finalizeMobileSigning
**Request Content**
''sh
{
"key": "transactionUUID",
"timeout": ""
}
| Feature | Description |
|---|---|
| key | Initialize(initiated) process UUID |
| timeout |
Answer Information
''sh Signed Document in Base64 format "MIIK8wYJKoZIhvcNAQcCoIIK5DCCCuACAQExDTALBglghkgBZQMEAgMwKAYJKoZIhvcNAQcBoBsEGXRlc3QgZG9r"
## **Cades Signing**
Cades signature type is a signature type that is thrown to all document types (mp3, mp4, png, txt, etc.). Integrated, Discrete, Serial, and Parallel signatures can be made in this signature type.
The requests shown in the signing operations above can be used for this method.
### **Integrated Signature**
An integrated signature is a format in which the signed document and signature information are kept together. In the KamuSM - Digital Signature project, the **embeddedSignature** parameter in the signing request must be passed as **true** to sign in this format.
### **Disjoint Signature**
To get a disjoint signature, the **embeddedSignature** parameter must be passed as **false**.
### **Serial Signature**
A serial signature is a signature that is signed. The document to be signed is also used to determine signature levels.
```>``` The parallel and serial option does not matter in the first signature, but the parallel and serial option can be used when a second signature is desired to be signed on a document with one signature.
The **isCounter** parameter must be passed as **true** in order to sign a series.
### **Parallel Signature**
A type of signing with equal signature levels. In this method, if a second signature is made, it is equal to the first signature in terms of level.
The **isCounter** parameter must be passed as **false** in order to sign a series.
## **Cades Signature Verification**
A request is made to the **verify** method of the CadesController to perform Cades signature verification.
**Request Address**
''sh
http://localhost:3638/api/cades/verify
Request Content
''sh { "file":"63D1770A9143729C62962FC5599D0609D709343D5E299D8E71", "existSignature":"Q5eaPK/4RPUhDJlzioDsNo6SxFojpBRe9ivC+Ss0rVI" }
| Feature | Description |
|----------------|-------------------------------------------------------------------------|
| file | Unsigned document or disjointed signed document |
| existSignature | Signature information of a separately signed document |
**Answer Information**
''sh
Returns True if the file is signed or False if it is not signed.
true / false
> For files that are signed integrated, it is sufficient to send only file information.
> In the case of separately signed files, it is necessary to make a request with the file itself and signature information.
Pades Signing
Integrated Signature
An integrated signature is a format in which the signed document and signature information are kept together. In the KamuSM - Digital Signature project, the embeddedSignature parameter in the signing request must be passed as true to sign in this format.
> Pades signing does not have the Serial signature, Parallel signature, and Disjoint signature options.
Pades Signature Verification
A request is made to the verify method of the PadesController to perform Pades signature validation.
Request Address
''sh http://localhost:3638/api/pades/verify
**Request Content**
''sh
{
"file":"63D1770A9143729C62962FC5599D0609D709343D5E299D8E71",
}
| Feature | Description |
|---|---|
| file | Signed document |
Answer Information
''sh Returns True if the file is signed or False if it is not signed. true / false
```>``` For files that are signed integrated, it is sufficient to send only **file** information.
```>``` Also, Pades does not receive existSignature information because the signature is only Integrated.
## **Xades Signing**
### **Integrated Signature**
An integrated signature is a format in which the signed document and signature information are kept together. In the KamuSM - Digital Signature project, the **embeddedSignature** parameter in the signing request must be passed as **true** to sign in this format.
### **Disjoint Signature**
To get a disjoint signature, the **embeddedSignature** parameter must be passed as **false**.
### **Serial Signature**
The **isCounter** parameter must be passed as **true** in order to sign a series.
### **Parallel Signature**
A type of signing with equal signature levels. In this method, if a second signature is made, the first signature is equal in level.
### **Enveloped Signature**
XML data contains the signature in it. In order to sign this type, it is necessary to pass the **isEnveloped** parameter as **true**.
```>``` Xades signature has the **fileName** parameter, which is different from other signature types. This parameter is written to the file that is created when the disjoint signature is created, and the XML file is referenced during validation using **fileName**.
## **Xades Signature Verification**
A request is made to the **verify** method of XadesController to perform Xades signature verification.
**Request Address**
''sh
http://localhost:3638/api/xades/verify
Request Content
''sh { "file":"63D1770A9143729C62962FC5599D0609D709343D5E299D8E71", "existSignature":"Q5eaPK/4RPUhDJlzioDsNo6SxFojpBRe9ivC+Ss0rVI", "fileName":"test" }
| Feature | Description |
|----------------|-------------------------------------------------------------------------|
| file | Unsigned document or disjointed signed document |
| existSignature | Signature information of a separately signed document |
| fileName | The file name of the signed document. |
**Answer Information**
''sh
Returns True if the file is signed and False if it is not signed.
true / false
> For files that are signed integrated, it is sufficient to send only file information.
> In the case of separately signed files, it is necessary to make a request with the file itself and signature information.
> In addition, fileName is needed when validating the Xades signature.
Signature Archiving
Request Address
> Whatever type of file we want to archive, a request should be sent to that address.
''sh http://localhost:3638/api/cades/archive http://localhost:3638/api/xades/archive http://localhost:3638/api/pades/archive
**Request Content**
''sh
{
"file": "AgMC4wIDAuMCAwLjBdCj4+++CnN0YXJ0eHJlZgoxN...",
"whiteList": [
"SHA512"
],
"timeStampHost": "timeStampHost",
"timeStampUser": "timeStampUser",
"timeStampPassword": "timeStampPass"
}
| Feature | Description |
|---|---|
| file | Signed document |
| whiteList | Secure Hash Algorithm information |
| timeStampHost | Timestamp host address |
| timeStampUser | Timestamp username |
| timeStampPassword | Timestamp password info |
| fileName | Name of signed file |
> when archiving Xades, fileName must be sent in addition to these parameters.
Signature Upgrade
Request Address
> Whatever type of file we want to upgrade, a request should be sent to that address.
''sh http://localhost:3638/api/cades/upgradeSignature http://localhost:3638/api/xades/upgradeSignature http://localhost:3638/api/pades/upgradeSignature
**Request Content**
''sh
{
"file": "",
"existSignature":"",
"signatureType": 2,
"timeStampHost": "timeStampHost",
"timeStampUser": "timeStampUser",
"timeStampPassword": "timeStampPass"
}
| Feature | Description |
|---|---|
| file | Signed document |
| existSignature | Signature information of a separately signed document |
| signatureType | The level we want to raise the signature to |
| timeStampHost | Timestamp host address |
| timeStampUser | Timestamp username |
| timeStampPassword | Timestamp password info |
| fileName | Name of signed file |
> When upgrading a Xades signature, fileName must be sent in addition to these parameters.
| Numeric Value | Signature Type |
|---|---|
| 0 | BES |
| 1 | EST |
| 2nd | ESXLONG |
| 3rd | ESA |
> In the sample request, the signature was requested to be translated into ESXLONG.
> Hierarchical order should be considered when assigning an elevation request. For example, a level 2 signature cannot be upgraded to level 1. But it can be upgraded to level 3.
Enhanced Signature Verification
> Whatever type of file we want to verify, a request should be sent to that address.
''sh http://localhost:3638/api/cades/verifyAndReturnSignatureInfos http://localhost:3638/api/xades/verifyAndReturnSignatureInfos http://localhost:3638/api/pades/verifyAndReturnSignatureInfos
**Request Address**
''sh
http://localhost:3638/api/cades/verifyAndReturnSignatureInfos
Request Content
''sh { "file":"63D1770A9143729C62962FC5599D0609D709343D5E299D8E71", "existSignature":"Q5eaPK/4RPUhDJlzioDsNo6SxFojpBRe9ivC+Ss0rVI" }
| Feature | Description |
|----------------|-------------------------------------------------------------------------|
| file | Unsigned document or disjointed signed document |
| existSignature | Signature information of a separately signed document |
**Answer Information**
''sh
{
"signatures": [
{
"certificate": {
"data": "Uw4f4PRdyg46GthksH+C5WAgp3kCoBbUzPA2cR7i1roSxq/KCfk2ch0aMJw=="
},
"signType": "TYPE_BES",
"signOwner": "EROL ERYİĞİT",
"signOwnerDescription": "CN=Name Surname,L=İL Info,C=TR,SERIALNUMBER=TCKN",
"identifierID": "40627698990",
"contentType": null,
"digestAlgorithm": "SHA512",
"signatureAlgorithm": "[RSA-with-SHA512,null]",
"policyOID": null,
"signDate": "2022-11-06T21:45:31.000+00:00",
"timeStamp": null,
"archiveTimeStamps": null,
"hasTimeStamp": false,
"hasArchiveTimeStamps": false,
"moneyLimit": "10000.0",
"qCStatements": null,
"isValid": true,
"isQualified": true,
"isSignatureValid": null,
"isCounterSignature": false,
"contentHint": null,
"commitmentType": -1,
"contentIdentifier": null,
"signerLocation": null,
"contentTimeStamp": null,
"policyAddress": "",
"contentReference": null,
"requiresArchival": null
}
],
"timeStamp": null,
"isValid": true,
"validationDescription": "All signatures in the Signed Data have been verified.",
"validationDetail": "1. Signature is checked. \nResults:\nSigner Certificate:CN=EROL ERYİĞİT,L=KOCAELİ,C=TR,SERIALNUMBER=40627698990\nPre-verification is done.\nSignature Checker Results:\n(+) Signature Checker\n\tSignature crypto verification is successful.\n(+) Message Digest Attribute Checker\n\tMessage digest check is successful.\n(+) Signing Certificate V2 Attribute Checker\n\tSigning certificate attribute check is successful.\n(+) Certificate Validation Checker\n\tCertificate validation is successful\n(+) Content Type Attribute Checker\n\tContent Type attribute check is successful.\n"
}
| Feature | Description |
|---|---|
| data | Information of the certificate in hex format |
| signType | Type of signed document |
| signOwner | Signatory Name-Surname |
| signOwnerDescription | NameSurname, province, Country and TCKN information |
| identifierNo | TCKN Information |
| contentType | Content Type |
| digestAlgorithm | digestAlgorithm type |
| signatureAlgorithm | signatureAlgorithm type |
| policyOID | Policy ID |
| signDate | Signed Date |
| timeStamp | Timestamp Info |
| archiveTimeStamps | Archive Timestamp Information |
| hasTimeStamp | Timestamped or not information |
| hasArchiveTimeStamps | Archive timestamp information |
| moneyLimit | Money Limit |
| qCStatements | ... |
| isValid | Signature accuracy information |
| isQualified | Is Qualified for Certification |
| isSignatureValid | signature accuracy information |
| isCounterSignature | Serial signature information |
| contentHint | Insider tip |
| commitmentType | ... |
| contentIdentifier | Content identifier |
| signerLocation | Signer Position |
| contentTimeStamp | Content timestamp |
| policyAddress | Policy Address |
| contentReference | Content reference to |
| requiresArchival | Archive information |
Possible Errors
We could not find the equivalents of some of our parameters in advanced signature verification in the KamuSM library. As a result of our negotiations with KamuSM, we will add these missing parameters to our developments. For example, information such as signerLocation, contentReference is now null.
Future Enhancements
The Digital Signature project has been developed by Bimser Solution and will continue to be developed. Our development goals include Mobile Signature signature support and a signature application with an interface that the end user can use.
Mobile Signature Integration
Mobile signature integration will be our first development in the future and signing transactions can be made from Turkcell, Türk Telekom and Vofadone operators.
Signature Interface App
Our interface application will appeal to end users other than developers. Through this interface application, users will be able to sign, verify and upgrade with a click.
Completion of missing parameters
In the Detailed Signature Verification section, the equivalents of some parameters are null. These parameters will be filled in when the KamuSM equivalents of these parameters are provided.
Supported/Unsupported File Types and Signature Types
| File Type | File Format | BES | EPES | EST | ESC | ESX_v1 | ESX_v2 | ESXLong | ESXLong_v1 | ESXLong_v2 | ESA | ESA_v2 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Pades | + | + | + | - | - | - | + | - | - | + | - | |
| Xades | xml | + | + | + | - | - | - | + | - | - | + | - |
| Cades | .*(all formats) | + | + | + | - | - | - | + | - | - | + | - |
At the basic level, the types we support are sufficient in the first stage to perform signature operations. Descriptions of the types we support in this table are as follows.
FIVE
Five signatures is a standard signature. The document contains only signature information. It is only known who signed the document.
EST
The feature that distinguishes the EST from the PPS is that in the signing process, information about when the signature was added is also included. This information about when it was signed is called a timestamp.
ESXLong
The ESXLong signature is also an EST signature. Unlike the EST signature, the ESXLong signature contains the verification data that will be used for certificate validation within the signature.
ESA
The ESA type signature is a type of signature developed against the loss of reliability of cryptographic algorithms over time. The algorithms we rely on now may become unreliable in 5-10 years. Before these algorithms become untrusted, signatures must be translated into the ESA type. However, translating the signature into ESA immediately after the signature is signed does not provide additional security.
How to Contribute
One of the different purposes of the Digital Signature project is to provide development infrastructure to users who want to make development. All the code used in the project has been shared with open source code for all users to shape and use as they wish. In this respect, the first needs of users as development may be from the following options.
- Development of the other types that the KamuSM API supports, EPES, ESC, ESX_v1,ESX_v2, ESXLong_v1 ESXLong_v1 and ESA_v2 types on top of the signature types that we support in the basic sense,
- During the signature verification phase, all values returned from the KamuSM API are shown to the users without filter,
- Health check of the signature after signing (verification of the signature after signing),
can be improved.