eBA Two Factor Authentication (Google 2FA) Implementation
When you want to use the Google 2FA infrastructure while logging in to the eBA Mobile application, the following instructions must be followed.
Server-Side To-Do's
- Valid in current versions of eBA.
- The following keys should be added to the eBAConfiguration Editor
>Advanced>Security tab.
The CustomMFA field must be created and the MFAMode information must be set to Google.
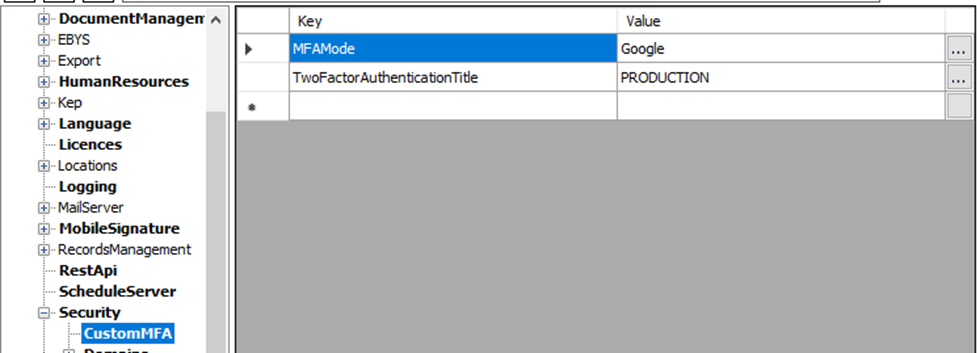 Image 1 eBA Configuration Editor Configuration
Image 1 eBA Configuration Editor Configuration
- There should be Turkish.txt
>English.txt files in the eBA Interface Document Management>system/settings/2FA mail templates folders. These files come with the relevant setup/update files.
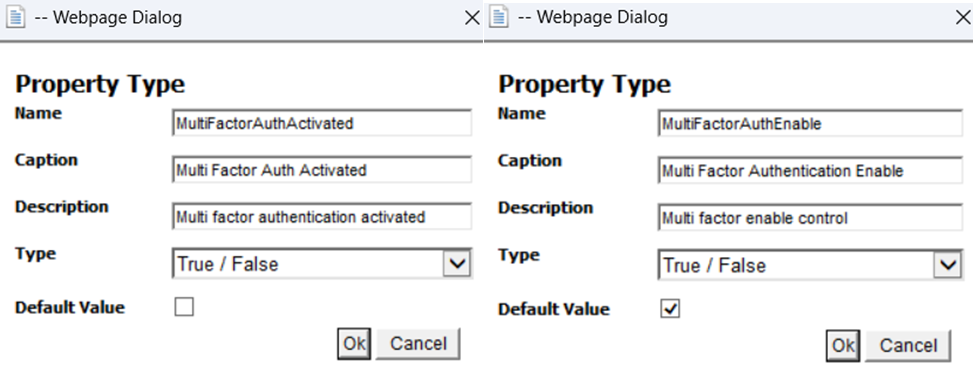
The properties specified in Figure 2 must be defined in the name of Multi Factor Authentication Enable and Multi Factor Auth Activated through eBA System Manager. Once this property is defined, it must be selected as a User Property.
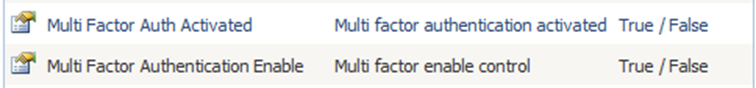 Figure 2: User Feature Identification
Figure 2: User Feature Identification
eBA System Manager > Property Definitions > Properties
MultiFactorAuthEnable is the property required for transactions to be active. MultiFactorAuthActivated is required for e-mail transactions containing barcode information for the user. This feature should be in a passive state at the time of adjustment. After all the settings are made, when the user wants to perform the login process, he receives an e-mail with barcode information. As soon as the mail is forwarded to the user, this feature is automatically activated and e-mails are prevented from being sent at each login. If the user is asked to send an e-mail again, this feature should be disabled in the user settings in System Manager. (Detailed information is available on Account Reset/Recovery processes)
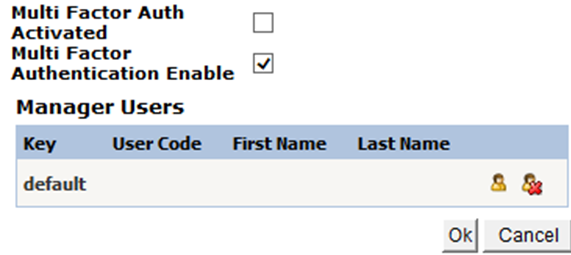
Figure 3: SystemManager setup settings.
Client-Side To-Do
- The current version of the eBA Mobile application, which can be downloaded from Google Play and/or Apple Store platforms, must be installed on the mobile device.
- The Google Authenticator application, which can be downloaded from the same platforms, must be installed on the mobile device.
Example Use Case
When trying to log in to eBA from their mobile device, the user will be asked for the 2FA Verification Key.
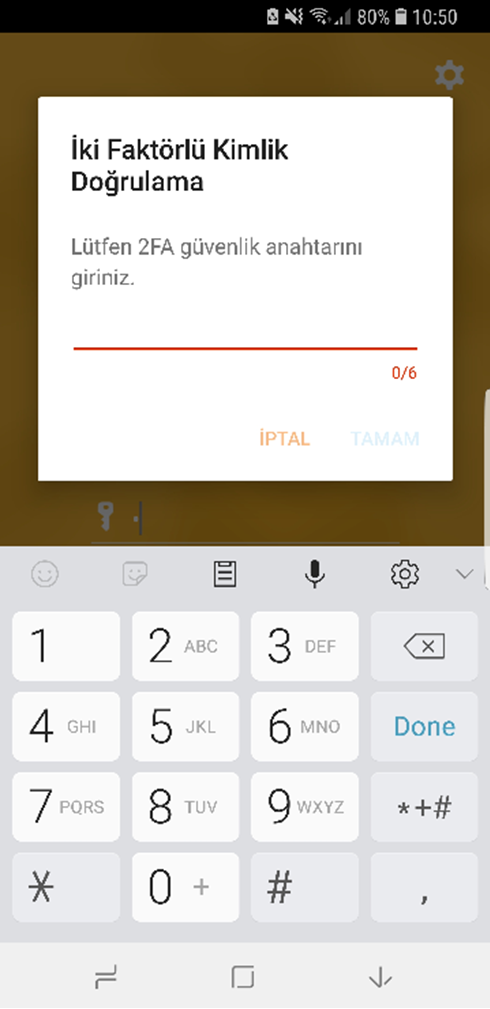
Figure 4: eBA Mobile Interface In order to use this code at the time of first login, the QR code sent to the user's e-mail address must be scanned into the Google Authenticator application installed on his mobile device.
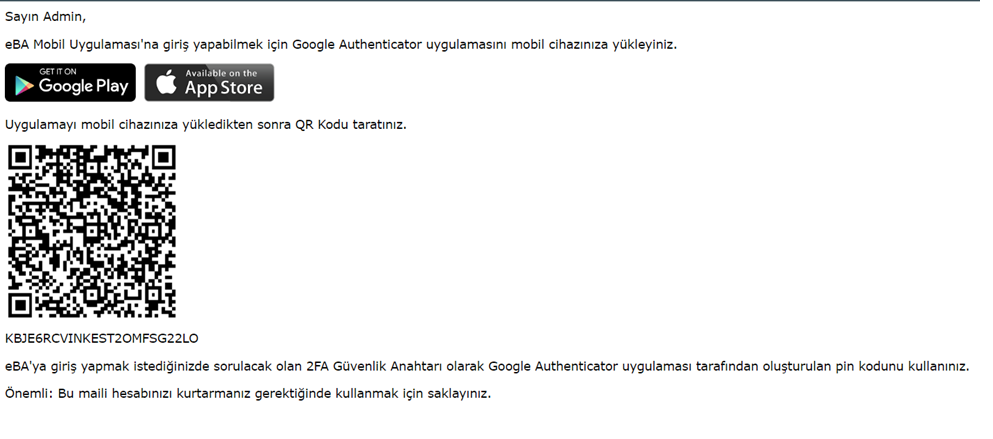
Image 5 Incoming Mail Content Thanks to this QR code, the Google Authenticator application will derive Verification Keys with periodic timeouts.
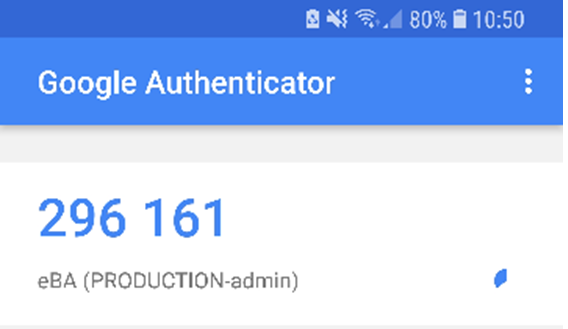
Image 6 Generated Verification Key The user who tries to log in to eBA from his mobile device logs in to eBA using the current verification key.
Account Reset/Recovery
In any case where the user loses the key defined by scanning the QR code if the user deletes the Google Authenticator application from his device, changes his device, etc., he can use it if he stores the first sent mail to be able to re-identify the QR code generated for his account.
If the mail has not been stored, for the system to send a QR code by mail again; By unchecking the Multi Factor Auth Activated feature defined for the user through the eBA System Manager, an e-mail is sent again on the first login attempt of the user.
eBA System Manager > Organization Management > Users > User Details
